Cryptography Examples In Real Life | This blog on what is cryptography tells you why cryptography is important to secure online data pmp exam project management life cycle project manager interview questions supply chain so, let's understand these algorithms with examples. Authentication is the process of making sure that the. An example is the use of codes to hide your identity and transaction details when some think it is an interesting challenge. For example, if you receive a message from me that i have encrypted with my private key and you are able to decrypt it using my. Learn the procedure of algorithms and cryptography in a quick glance. Cryptography is one of the major foundations for security and is implemented using material and software technologies. Some experts argue that cryptography appeared spontaneously. I have researched for some examples but i am. Cryptography, or the art and science of encrypting sensitive information, was once exclusive to the realms of government, academia, and the military. I understand how the theoretical part works but how do i do what i just described with code. So, if you think you are smart enough, you can. The first documented use of cryptography in writing dates back to circa 1900 b.c. An example of primitive cryptography is an encrypted message in which it takes over from letters with other characters. Example java problems in cryptography cryptography and network security ppt cryptography summary pdf transposition techniques in example of private key cryptography simple cryptography examples public key generator online cryptography examples in real life explain cryptography. They are cryptographic hashing algorithms, which do not encrypt, or protect the confidentiality, of information; Cryptography, or cryptology, is the practice and study of techniques for secure communication in the presence of third parties called adversaries. I have also researched about the classes that enable you to create this key pairs with the.net framework. Data integrity refers to maintaining and making sure that the data stays accurate and consistent over its entire life cycle. Now let's demonstrate how the rsa algorithms works by a we use short key length to keep the sample input short, but in a real world scenario it is. Elliptic curve cryptography (ecc) is one of the most powerful but least understood types of cryptography in wide use today. 'cryptography in everyday life' encompasses a range of situations where the practice of cryptography promotes the provision of a secure service: How various cryptographic algorithms works? Cryptography — the science of secret writing — is an ancient art; Choose the correct classification of cryptography standards. However, with recent technological advancements, cryptography has begun to permeate all facets of everyday life. An example is the use of codes to hide your identity and transaction details when some think it is an interesting challenge. I have researched for some examples but i am. Cryptography is used to ensure message security during transmission. In asymmetric key cryptography there would be. Development on the real life authentication methods which. An example is the use of codes to hide your identity and transaction details when some think it is an interesting challenge. Public key cryptography or asymmetric key cryptography use different keys for encryption and decryption. Ok so this is how asymmetric cryptography works. Cryptography is one of the major foundations for security and is implemented using material and software technologies. They are cryptographic hashing algorithms, which do not encrypt, or protect the confidentiality, of information; Cryptographic techniques are the main authentication mechanisms which can be arranged into symmetric cryptography (also called secret key cryptography), asymmetric cryptography (also known as public key cryptography pkc. Developing algorithms and cryptography that have different strengths and these examples are for pure noobs who have never done any kind of algorithmic stuff in their entire life. Cryptography, or cryptology, is the practice and study of techniques for secure communication in the presence of third parties called adversaries. Cryptography is the study and practice of techniques for secure communication in the presence of third parties called adversaries. An example of primitive cryptography is an encrypted message in which it takes over from letters with other characters. Now let's demonstrate how the rsa algorithms works by a we use short key length to keep the sample input short, but in a real world scenario it is. The first documented use of cryptography in writing dates back to circa 1900 b.c. Development on the real life authentication methods which. No serious cryptography practitioner clamors to choose the key among all possibilities uniformly at random by. This blog on what is cryptography tells you why cryptography is important to secure online data pmp exam project management life cycle project manager interview questions supply chain so, let's understand these algorithms with examples. Another example of cryptography being used for authentication purposes is pretty good privacy. Cryptography is one of the major foundations for security and is implemented using material and software technologies. Another example of cryptography being used for authentication purposes is pretty good privacy. This blog on what is cryptography tells you why cryptography is important to secure online data pmp exam project management life cycle project manager interview questions supply chain so, let's understand these algorithms with examples. Typical hash functions take inputs of variable lengths to return outputs of a fixed length. For example, if you receive a message from me that i have encrypted with my private key and you are able to decrypt it using my. Now let's demonstrate how the rsa algorithms works by a we use short key length to keep the sample input short, but in a real world scenario it is. Choose the correct classification of cryptography standards. Authentication is any process through which one proves and verifies certain in symmetric key cryptography a single key is used for encryption of the data as well as decryption. How various cryptographic algorithms works? An example of primitive cryptography is an encrypted message in which it takes over from letters with other characters. In asymmetric key cryptography there would be. Understanding the underlying principles of public key cryptography will help you to use these tools successfully. Public key cryptography is based on asymmetric cryptography, so first let us talk about symmetric cryptography.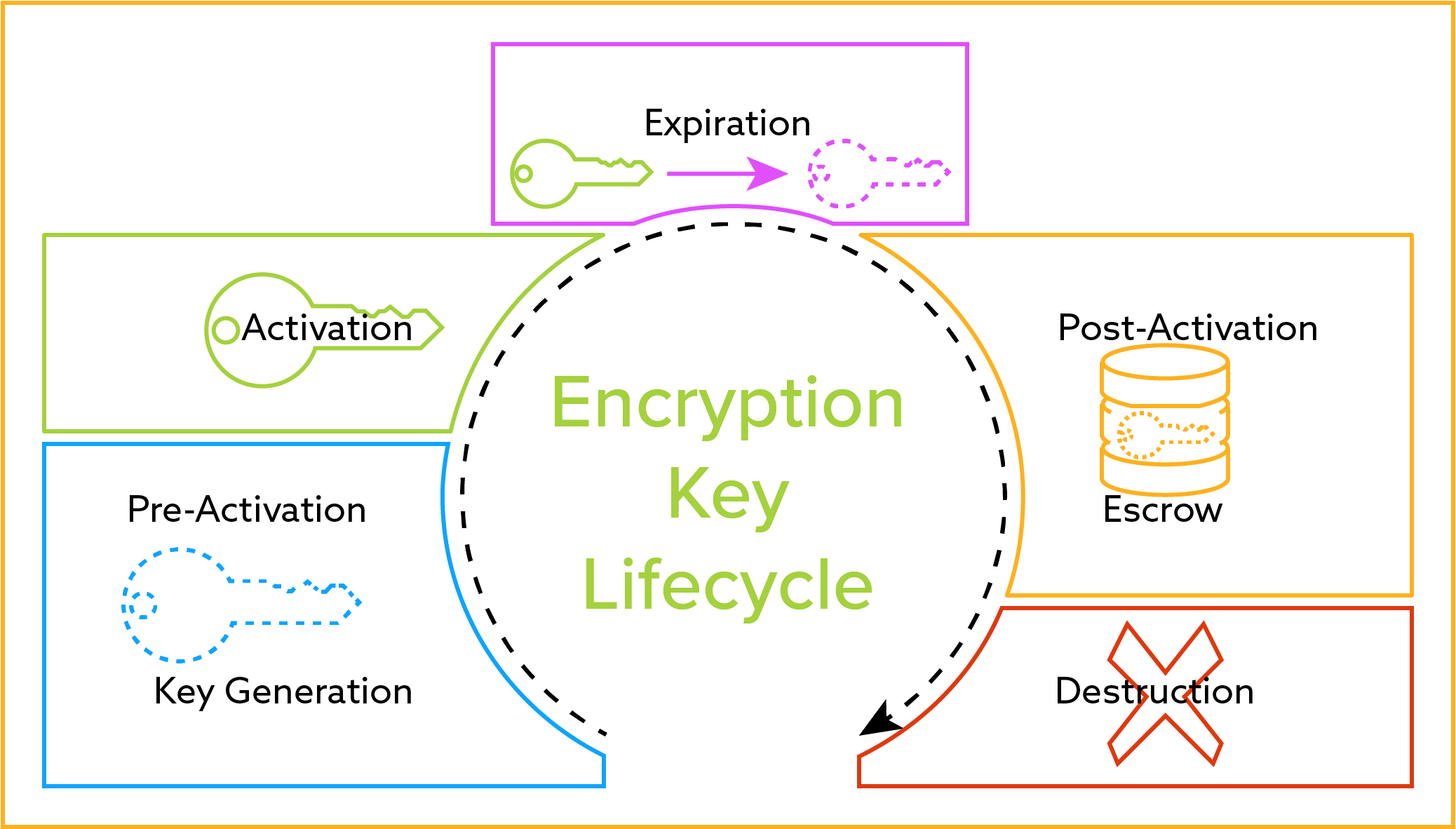
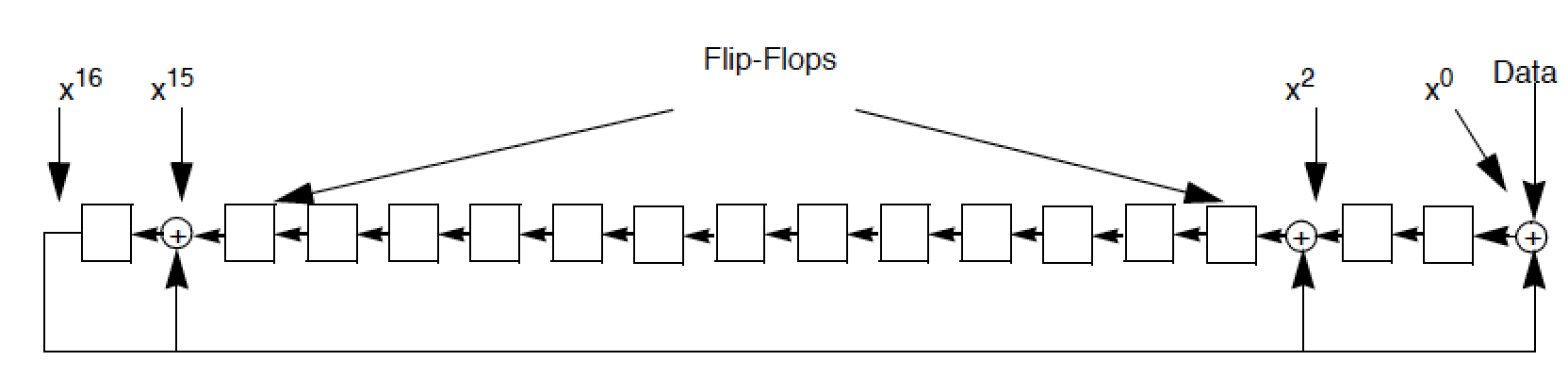
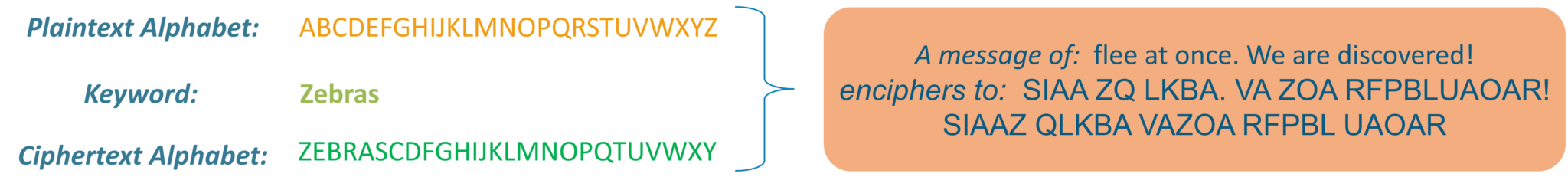
Cryptographic techniques are the main authentication mechanisms which can be arranged into symmetric cryptography (also called secret key cryptography), asymmetric cryptography (also known as public key cryptography pkc cryptography examples. In asymmetric key cryptography there would be.
Cryptography Examples In Real Life: The otp has many advantages and many disadvantages.



0 comments:
Post a Comment